Single_Packet_Authorization
Overview
Single Packet Authorization (SPA) is defined as the communication of authentication information over spa server port, together with the dynamic reconfiguration of a default-drop firewall policy to allow access to services that would otherwise be blocked, SPA communicates authentication information within the payload portion of a single packet. Because packet payloads are used, SPA offers many enhancements over PK such as stronger usage of cryptography, protection from replay attacks, minimal network footprint (in terms of what IDS’s may alert on - PK sequences look like port scans after all), the ability to transmit full commands and complex access requests, and better performance.
For simple, access service is blocked by firewall, SPA client requests to open that service for itself, SPA server authenticates the request, adds proper firewall rules to that client, after that client can access server as normal.
Workflow
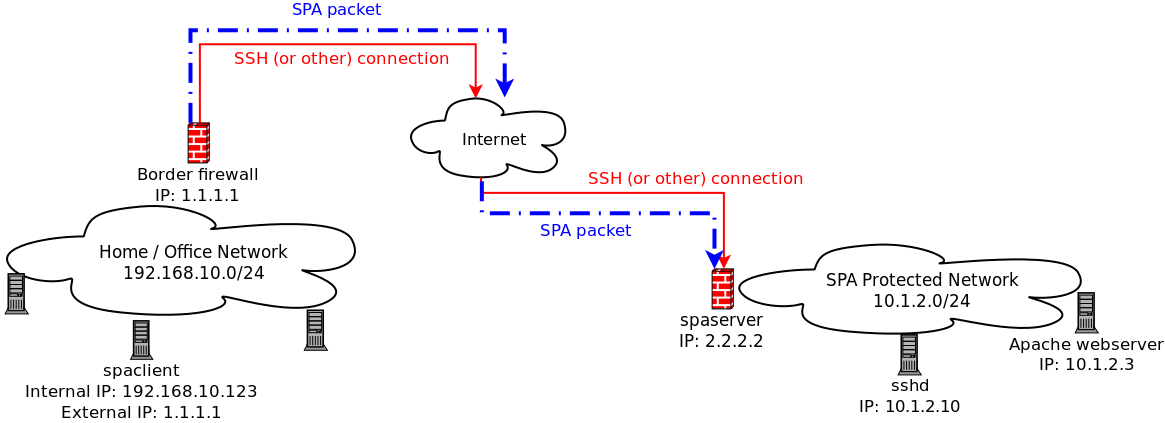
A basic outline for using fwknop to conceal an SSH daemon(or any service) with Single Packet Authorization (SPA) involves the following steps. This assumes an SPA client system (hostname: spaclient), and an SPA server system spaserver.domain.com where fwknopd is installed and the SSH daemon listens:
- Generate encryption and HMAC keys with fwknop –key-gen.
- Transfer the keys you just generated fwknopd to the server (this is where SSHD is listening too).
- Start fwknopd and deploy a default-drop firewall policy against all inbound SSH connections.
- From anywhere on the Internet, use the fwknop client to send an SPA packets and have fwknopd open the firewall.
- Use your SSH client as usual now that you have access. No one else can even see that SSHD is listening.
NOTE
- SPA sends request in payload to grant access(add firewall rule at spa server) for IP in the payload.
- Firewall(iptables) checks protocol headers for access.
Install
Here are the steps to install fwknop from source code, first make sure you have dev machine and env to compile from source, install from package is available for ubuntu as well, but here I want to share how to install from source.
install from package
1 | # Ubuntu18 |
install from source
1 | # install dependencies |
install server
1 | $ yes yes | git clone https://github.com/mrash/fwknop.git |
install client
1 | $ yes yes | git clone https://github.com/mrash/fwknop.git |
Examples
After installation, you need to config both client and server together to make them work, but the config depends on network topology you’re using, here are some typical use cases.
Network topology no NAT(same network or public ip), SPA server and service on same machine
server side
1 | # create key for hmac and aes |
client side
1 | # we use named config, the config file is at /user/.fwknoprc, create it if no |
Network topology with NAT, service(private address) behind SPA server on different machines
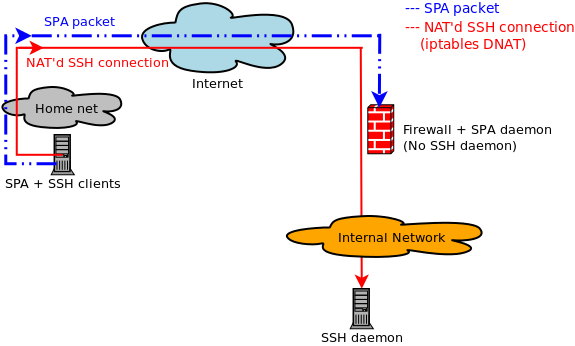
- client ip: 192.168.1.2
- SPA server ip: 10.10.10.3(public)
- SSH server ip: 192.168.100.10
server side
1 | # edit /usr/etc/fwknopd/fwknopd.conf |
client side
1 | $ cat /user/.fwknoprc |
Network topology with SNAT(at spa server), service behind SPA server on different machines
As you know SNAT is after POSTROUTING, that means when SPA server forwards packet, the SRC must be replaced, otherwise packet can not be routed to service server, it’s total SPA server config, client even not care!
1 | # edit /usr/etc/fwknopd/fwknopd.conf |
Network topology with DNAT(port only)
DNAT is needed when spa server does NOT want to grant access to well-known port like ssh(22), but instead grants access to a temporary port which is only known to SPA client who triggers the request for safe.
server
1 | # edit /usr/etc/fwknopd/fwknopd.conf |
client
1 | $ cat /user/.fwknoprc |
Grant access with limit scope(source ip, user, port)
By default, spa server allows ANY address with ANY user to request ANY port(on server) access, but we can limit the scope by several variables
server
1 | # edit /usr/etc/fwknop/access.conf |
client with user name
1 | $ cat /user/.fwknoprc |
troubleshooting
1 | # check service status |
FAQ
if client behinds NAT what special setting needed
As SPA server uses iptables which only see external IP used by client after SNAT, hence we should sent this ip in SPA packet.
1 | # edit /user/.fwknoprc at spa client, but never set ALLOW_IP which is the real ip in SPA message |