authentication_encryption
Overview
cryptography is about constructing and analyzing protocols that prevent third parties or the public from reading private messages; various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation are central to modern cryptography.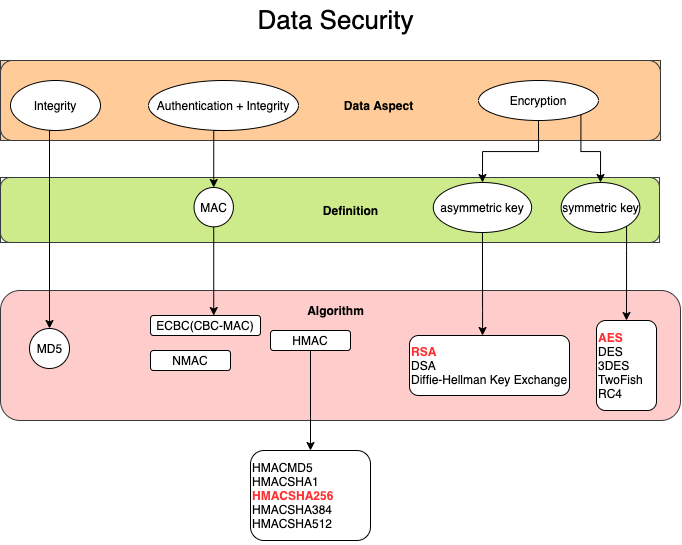
Data Integrity
In real world, something is sent along with message, make sure it’s not modified by the third party.
MD5
The MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value, this hash value sent out with message to protects a message’s data integrity, receiver uses MD5(algorithm) to calculate the hash value again, if it’s same with the one sent by sender, the data is not modified by someone else.
Authentication
MAC(message authentication code)
A message authentication code (often called MAC) is a block of a few bytes that is used to authenticate a message.
The MAC value protects a message’s data integrity,as well as its authenticity(because it uses private key as MAC input), by allowing verifiers (who also possess the secret key) to detect any changes to the message content.
here is workflow of MAC

The term message integrity code (MIC) is frequently substituted for the term MAC,especially in communications, to distinguish it from the use of MAC meaning MAC address (for media access control address).
MAC is the abstract part defined by RFC, In implementation, there are ways(algorithms) to calculate the code, that’s what you mostly see like HMAC, PMAC, OMAC, CMA, UMAC etc, HMAC is the most popular one.
HMAC
HMAC stands for hash-based message authentication code(the generated authentication code also called Digest). It is a specific type of MAC. It contains cryptographic hash functions and a secret cryptographic key. HMAC is capable of verifying data integrity and authentication of a message at the same time.
HAC(in implementation) has several algorithms to generate digest, here is a summary of that.
1 | hash algorithm digest length(bit) |
1 | Python 3.5.2 (default, Sep 10 2016, 08:21:44) |
Modern cryptography
Symmetric-key cryptography
Symmetric-key cryptography refers to encryption methods in which both the sender and receiver share the same key.
Implementation
- Twofish
- AES(Advanced Encryption Standard) original name: Rijndael
- Blowfish
- RC4
- DES
- 3DES
Public-key cryptography(asymmetric key)
A public key system is so constructed that calculation of one key (the ‘private key’) is computationally infeasible from the other (the ‘public key’), even though they are necessarily related. Instead, both keys are generated secretly, as an interrelated pair.
- Diffie–Hellman key exchange protocol
- DSS (Digital Signature Standard), which incorporates the Digital Signature Algorithm
- RSA encryption algorithm
- YAK authenticated key agreement protocol